When we developing the web applications that time need to
decide a strategy plan for authentication and authorization.
The strategy plan as given below.
- In the First steps, we need to identify the our application resources and the resources can be web pages, web services, HTML pages, data base and network etc.
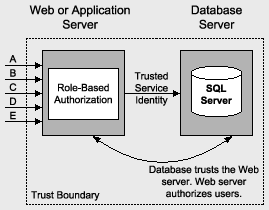
- In the second steps, we need to follow the strategy plan for applications authorization and the authorization strategy can be Role Based or Resources Based.
- In the third steps, we need to identify the resources which you are going to access the all layers of your application. The can be access by using the caller's identity, Process identity and Custom identity etc.
- In the fourth steps, we need to create the flow of the identity which you are going to use in the applications.
- In the fifth steps, we need to chose the authentication approached, The authentication approach is common scenarios for the web applications. It can be Identities, credential management (SQL Server databases, active directory etc.), browser type etc.